5.28.24 | by Van Graham

In today’s interconnected digital landscape, the notion of being completely immune to cyber threats is a myth that extends across governments, businesses, and individuals. Method Cyber Security’s recent audit for a leading financial services company underscores this reality while highlighting the critical role of proactive risk management in fortifying cybersecurity resilience.
The audit’s inception involved a meticulous process of risk identification, where Method Cyber Security collaborated closely with the company’s IT stakeholders to assess and analyze potential vulnerabilities. This encompassed a comprehensive review of network infrastructure, data handling protocols, third-party integrations, and employee cybersecurity practices. Noteworthy findings included outdated software systems, inadequate access controls, weak password policies, and gaps in endpoint security. These insights formed the foundation for subsequent risk assessment and mitigation strategies.
Building upon the insights gleaned from risk identification, Method Cyber Security conducted a thorough risk assessment to quantify and prioritize identified risks. Leveraging risk matrices and threat modeling frameworks, the team evaluated the potential impact and likelihood of various cyber threats.
Importantly, the audit revealed that the company had recently faced a cyberattack, although thanks to the deployment of state-of-the-art cybersecurity technologies, no data was exfiltrated. This incident underscored the critical need for robust risk management practices and proactive cybersecurity measures.
Armed with a detailed risk assessment, Method Cyber Security collaborated with the company’s IT and security teams to develop and implement targeted risk response strategies. These strategies encompassed a multifaceted approach, including:
These proactive measures aimed to not only mitigate existing vulnerabilities but also build a resilient cybersecurity framework capable of adapting to evolving threats.
The audit’s culmination involved the establishment of robust risk monitoring and management mechanisms. Method Cyber Security recommended the deployment of real-time monitoring tools, intrusion detection systems (IDS), and security incident response platforms. Continuous monitoring and analysis of network traffic, system logs, and user activities were emphasized to detect and respond swiftly to anomalous behavior or potential security incidents. Regular security audits, vulnerability assessments, and penetration testing were also recommended to ensure ongoing compliance and readiness to combat emerging cyber threats.
The audit served as a catalyst for organizational transformation, instilling a proactive cybersecurity mindset and fostering a culture of risk-awareness within the company. The transition to WebAuth significantly reduced the company’s susceptibility to social engineering attacks and enhanced overall authentication security. Importantly, the incident where no data was exfiltrated despite a cyberattack highlighted the efficacy of state-of-the-art cybersecurity technologies and risk management strategies.
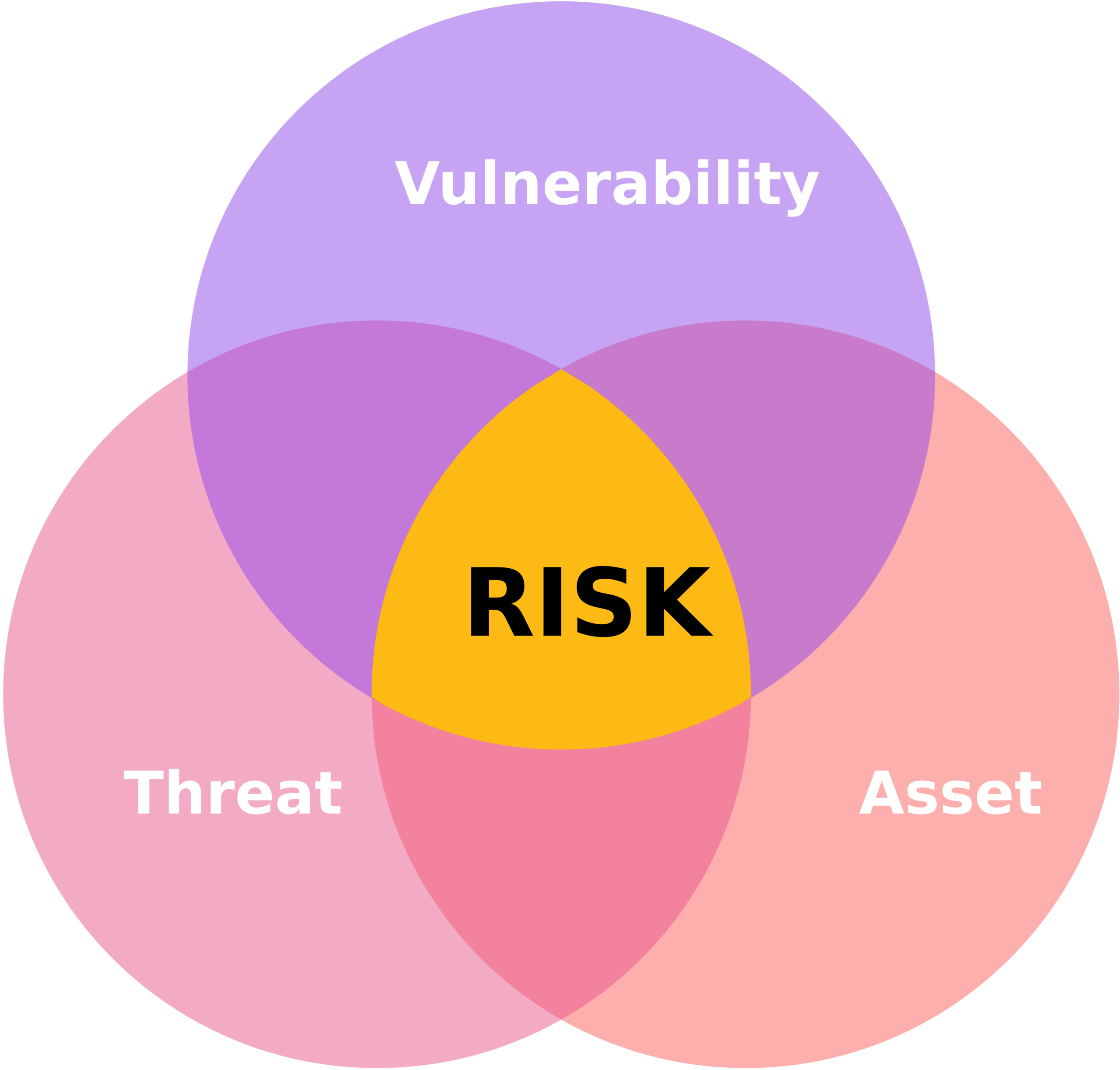
In conclusion, Method Cyber Security underscores the continuous evolution of cybersecurity practices and the imperative of integrating robust risk management frameworks into organizational strategies. By prioritizing cybersecurity resilience, leveraging advanced technologies, and fostering a culture of security awareness, organizations can navigate the complex cybersecurity landscape with confidence, ensuring a secure digital ecosystem for all stakeholders.
|