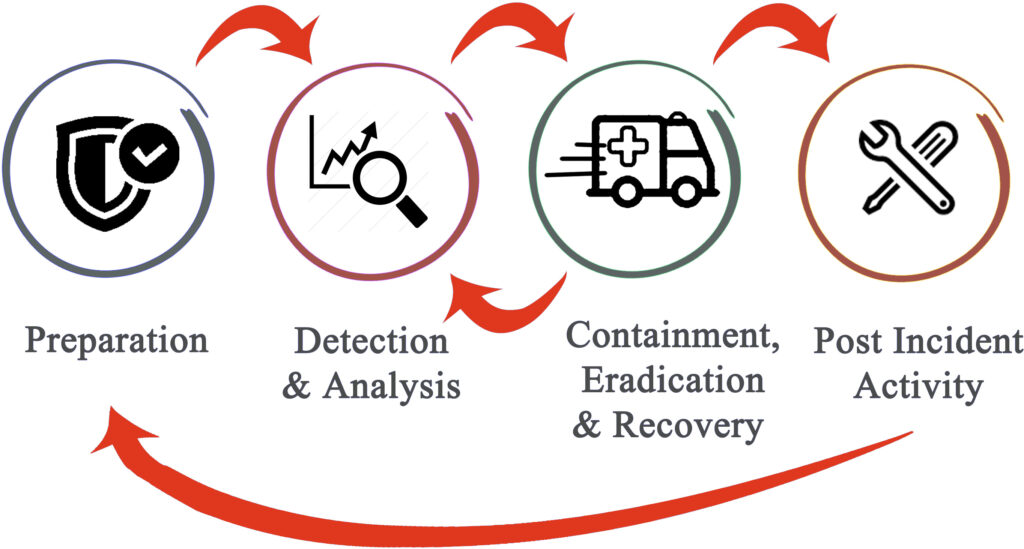
A security breach, according to NIST, is a violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices whether written or common knowledge. These incidents are clearly discerned from normal system use events and adverse events, such as, system or network malfunctions.
Security breaches occur in a virtually unlimited number of ways; therefore, it is not possible to institute a step-by-step procedure for responding to every incident. It is nevertheless imperative to develop an effective computer security incident response plan, so that the incident responses are performed quickly and effectively.
Security breaches almost always compromise your critical business data. An incident response plan helps to minimize loss or theft of information and disruption of business continuity. Keeping the number of incidents reasonably low is very important to protect the business processes of the organization. If security controls are insufficient, higher volumes of incidents may occur.