With the proliferation of personal information available on the Internet, your secret questions could be failing you. For one, there are a multitude of websites housing large databases of your historical information. BeenVerified is only one of many websites whose focus is collecting and publishing, for profit, information about you collected and consolidated from a variety of public resources. Your birthdate, location of birth, mother’s maiden name, father’s middle name, the street you grew up on, and more are all openly available.
Further weakening your secret questions, identity thieves and hackers are polling social media to obtain more background information about you. The graphics below depict hackers attempting to gather answers to your secret questions. The McDonalds Facebook post clearly shows over 1.1 million users providing their first employment to these scammers. Both your first job and first car are common secret questions.
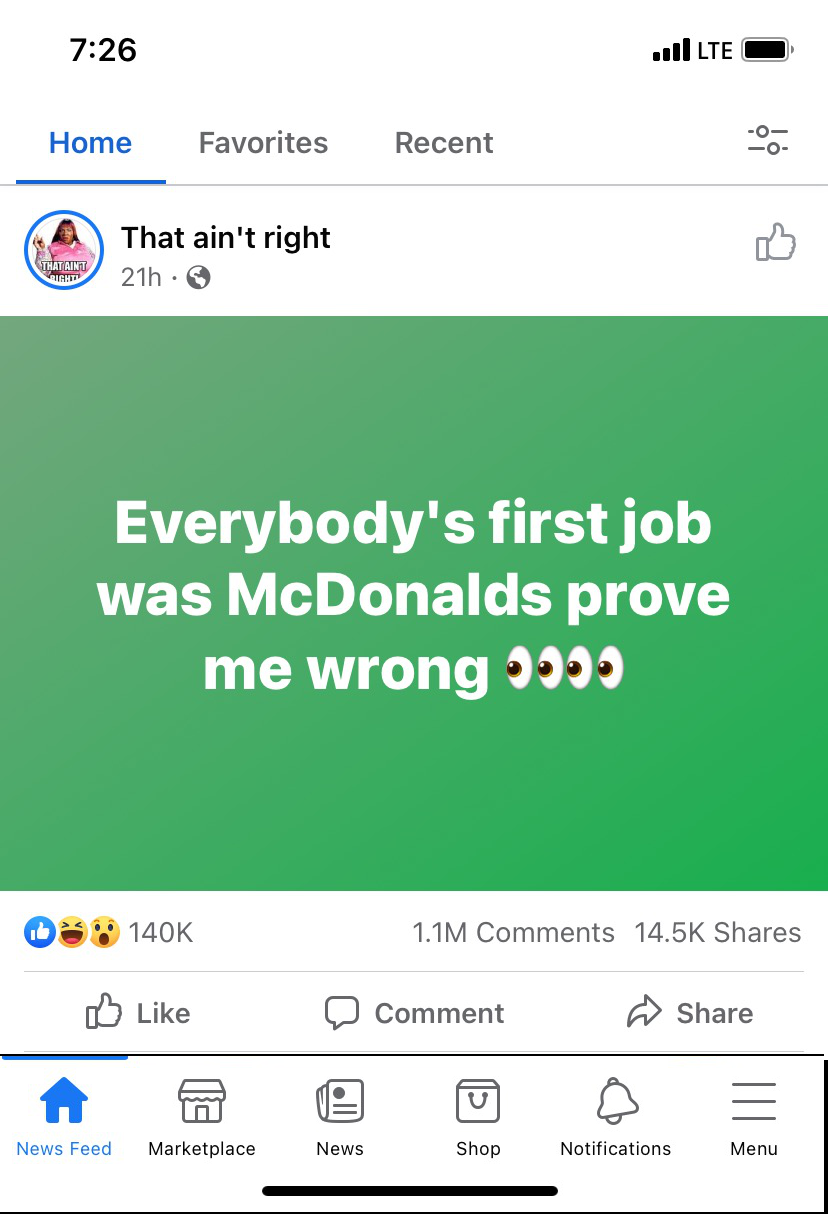

Because these posts were public, responding, even sarcastically, will expand their reach to others that may not realize it is a scam. Take extreme care when sharing information on social media.
Solutions to the vulnerability of secret questions, password generation and management, and multi-factor authentication will be available in the upcoming post titled “Are We Safe from Hackers?“
Written by Lance Fogarty, Senior Digital Examiner at Method Forensics
September 27, 2021